#Database Processing Fundamentals Design
Explore tagged Tumblr posts
Text
SysNotes devlog 4 - Editing profiles (part 1)
Welcome back to my SysNotes update! SysNotes is a system management app for people with DID, OSDD, and those who are otherwise plural.
This is part 1 of 3(?) about editing profiles. I have broken them down into somewhat equal length scopes:
Edit the header and image; fundamentals of the editing logic; design justifications
Edit description, history, characteristics (traits, likes, dislikes, triggers), relationships, and categories
Adding custom statuses, characteristics, relationships, and categories
First Devlog (1) | Previous Devlog (3)
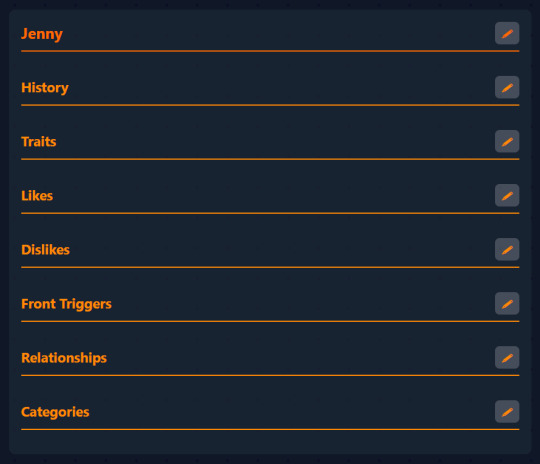
Editing profiles
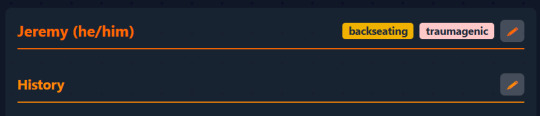
You see this little icon in the corner of a profile?

Originally, this was the icon for toggling edit mode for the entire profile. This means transforming all the text into textboxes and showing the interface for populating empty sections. However, I don't think that is the most elegant approach. It also would be quite messy computationally, because every time you wanted to edit one field the app would need to validate and process all the other fields in addition to the one you edited before it was able to save it.
So what I propose to do now is to have a separate edit icon for each individual section so that you can edit them selectively. To be able to edit the sections I will need to display them all, each with their own edit icon:
(The reason the first line is a darker orange is because it's a main heading, and the other lines are subheadings)
Editing header & main editing logic
Ok, let's transform the name into a textbox when the button is clicked.
First, I created a variable to track whether the user is editing the header or not. At the start, it is set to false:

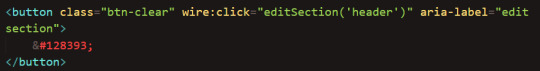
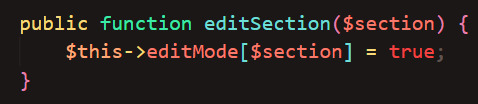
Then, I created a function that sets the variable to true when the edit button is clicked:
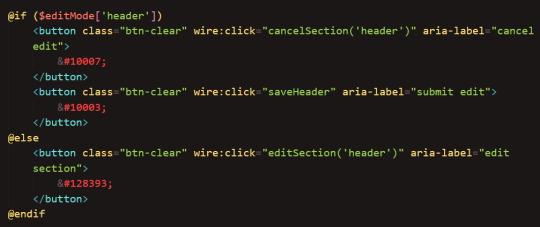
(& #128393; here is just the pencil emoji symbol code; "clear" in "btn-clear" refers to the background transparency, not the action of clearing)
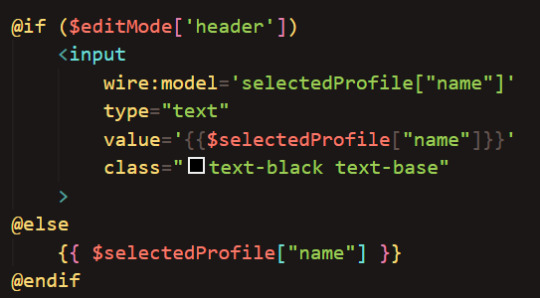
Finally, in my component I check if edit mode is on. If so, a textbox is rendered. If not, it displays just the text:
("@if ($editMode['header'])" is logically the same as "@if($editMode['header'] == true)")
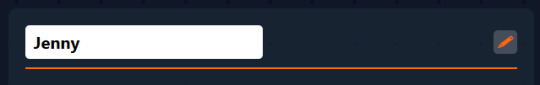
One issue I ran into is that Livewire doesn't actually work correctly with associative arrays such as "$selectedProfile['name']" (when I clicked save, the whole component would stop displaying). So I had to assign the name to a temporary variable called "tempName" for it to be able to refresh correctly.
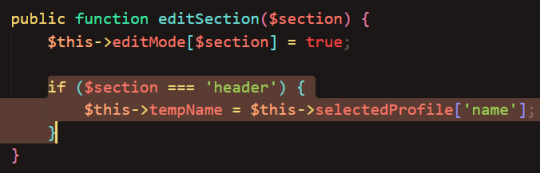
(And then I had to update the textbox to reference tempName)
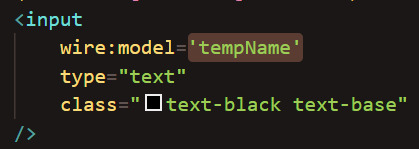
Annoyingly, that means I would need to create a separate variable for each editable field instead of dynamically assigning them from the profile itself. It's messy, but it works so I'll roll with it.
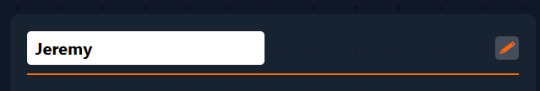
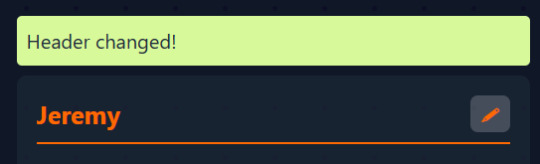
Now that we're back on track, let's say Jenny is trans and wants a more masc name, like Jeremy:
Now we need a way to save the new name. Let's add a "submit" and "cancel" buttons when the edit mode is on:
(Again, the codes in red represent the ✔ and ✗ symbols)
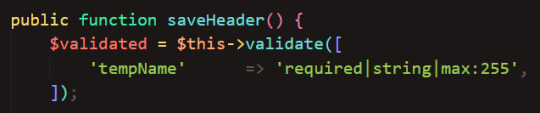
For the new name to actually save, we need to validate it to make sure the database can accept it. I copied the validation code from devlog 3 :
(The save code is boring so I'll skip it, I bet you're so sick of code by now) xD
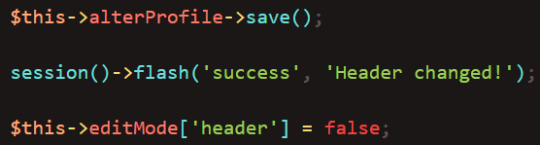
After the name is saved, we need to add a success message and turn off edit mode:
Rinse and repeat (header)
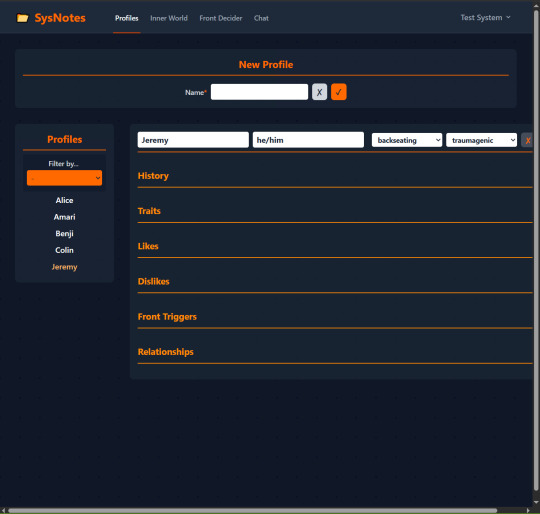
Now if you remember, the header has 4 pieces of information: name, pronouns, status, and origin.
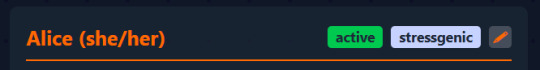
I can follow the same process to create an edit view for the rest of the header components. Now we can add pronouns, status, and origin to the new profile, as well as edit them later:

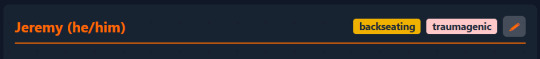
Drop-downs
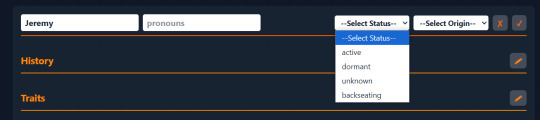
I want to show how I did the status and origin dropdowns because I think it's cool, and not overly complex. First, I initialized the variables that will store a list of statuses/that are available to the user.
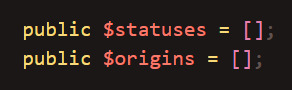
Then, I did a database query for each one, basically getting the statuses/origins that either have an owner ID of null (available to all users) or an owner ID of the user's ID (custom-added by the user). This is so that you don't have access to another user's custom statuses/origins.
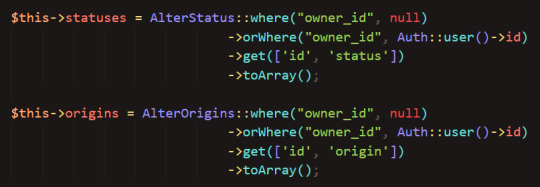
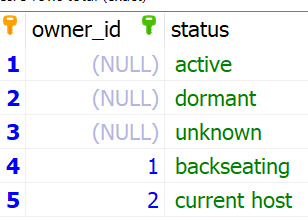
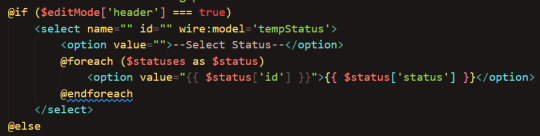
Finally, I iterated over the array (list) of statuses (and origins) and added a dropdown option for each status/origin in the array:
Responsive design (narrow screens)
I haven't really started to work on the mobile design yet, however my header isn't quite fitting on my screen even on desktop:
To make it easier to give edit mode and view mode different layouts, I separated them into 2 parts. As you can see, one is displayed if the edit mode is off, and the other displays if the edit mode is on:
(" @if (!$editMode['header'])" is equivalent to "@if ($editMode['header']) == false" (specifically the "!" symbol))
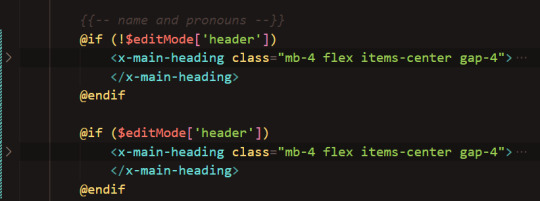
Next, the CSS framework Tailwind that I'm using for styling has screen breakpoints built in. Here, I used "md:" to display the inputs in 2 columns from medium widths onward, and "xl:" to display the inputs in 4 columns from extra large screens onward. Since I didn't specify the column number for small screens, the inputs will display in one column by default.
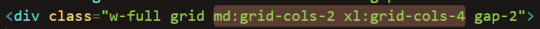
(Medium screen:)
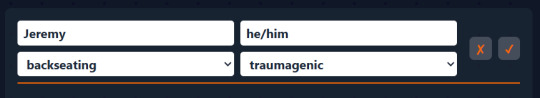
(Extra large screen:)

Editing profile image
If you compare a filled profile with the new profile, you'll see that the profile image and description don't have their own headings to attach an edit button to. Having headers wouldn't make sense as the name is already a header for the character bio (image + description).
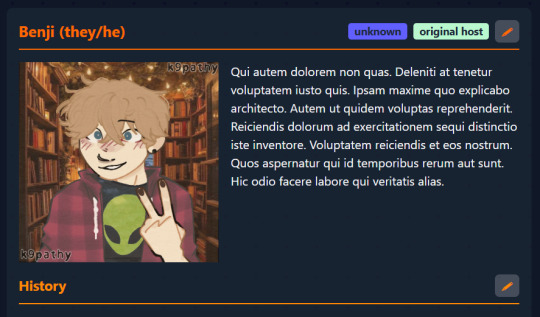
So where would I squeeze in 2 extra edit buttons, and how would the user know which parts of the profile they're for?
My solution was to add placeholders where the image and the description text would go!
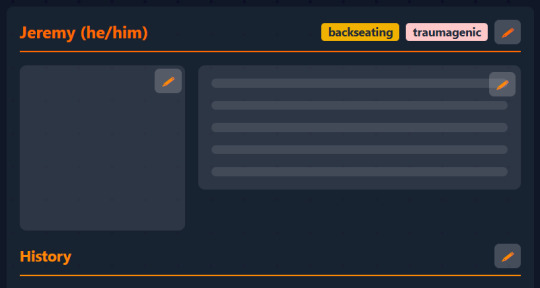
...Aaaand I have just reached the image limit for this post, oops. We're almost at the end of the devlog so that should be alright. All I need to do now is save the image to the database the same way I saved the name etc, and that's this part done!
I will cover editing the description and history in the next devlog as I have some things to say about their format, see you then!
7 notes
·
View notes
Text
In early May, the Environmental Protection Agency announced that it would split up the agency’s main arm devoted to scientific research. According to a report from NPR, scientists at the 1,500-person Office of Research and Development were told to apply to roughly 500 new scientific research positions that would be sprinkled into other areas of the agency—and to expect further cuts to their organization in the weeks to come.
This reorganization threatens the existence of a tiny but crucial program housed within this office: the Integrated Risk Information System Program, commonly referred to as IRIS. This program is responsible for providing independent research on the risks of chemicals, helping other offices within the agency set regulations for chemicals and compounds that could pose a danger to human health. The program’s leader departed recently, ahead of the restructuring announcement.
The EPA’s reorganization, experts say, will likely break up this crucial program—which has been targeted for decades by the chemical industry and right-wing interests.
“Unfortunately, right now, it looks like the polluters won,” says Thomas Burke, the founder and emeritus director of the Johns Hopkins Risk Sciences and Public Policy Institute and a former deputy assistant administrator of the EPA’s Office of Research and Development.
“The May 2 announcement is all part of a larger, comprehensive effort to restructure the entire agency,” EPA spokesperson Molly Vaseliou told WIRED in an email. “EPA is working expeditiously through the reorganization process and will provide additional information when it’s available.”
Formed in the mid-1980s, the IRIS program was designed to investigate the health impacts of chemicals, collating the best available research from across the world to provide analyses of potential hazards from new and existing substances. The program confers with other offices within the EPA to identify top chemicals of concern that merit further research and study.
Unlike other offices in the EPA, the IRIS program has no regulatory responsibilities; rather, it exists solely to provide science on which to base potential new regulations. Experts say this insulates IRIS-produced assessments from outside pressures that could influence research done in other areas of the agency.
“There’s independence” in being in a centralized program like IRIS, says Jennifer Orme-Zavaleta, also a former principal deputy assistant administrator of the Office of Research and Development and a former EPA science adviser. “They’re not trying to evaluate risk for a specific purpose. They’re just evaluating risk and providing fundamental information.”
Since its inception, IRIS has created a database of more than 570 chemicals and compounds with assessments of their potential human health effects. This body of research underpins not just federal policy, but helps guide state and international regulations as well.Got a Tip?Are you a current or former government employee who wants to talk about what's happening? We'd like to hear from you. Using a nonwork phone or computer, contact the reporter securely on Signal at mollytaft.76.
The IRIS database is the “gold standard for health assessments for chemical pollutants,” says Burke. “Virtually all of our regulated pollutants, virtually all of our cleanups, virtually all of our major successes in regulating toxic chemicals were touched by IRIS or the IRIS staff.”
Yet IRIS has faced a significant uphill battle in recent years. For one, there’s the sheer number of chemicals it has had to review with limited manpower. There are more than 80,000 chemicals that have been registered for use in the US, and chemical companies register hundreds more each year. Some of the chemicals IRIS is working to research have been substances of concern for years, while some have more recently drawn new scrutiny. For instance, forever chemicals—synthetic materials so named because of their persistence in the environment—have been in use for decades, but their recent prevalence in tests of water and soil prompted IRIS in 2019 to begin creating draft assessments for five common types of these chemicals.
Opposition from industry has also bogged down IRIS reviews. The very existence of the IRIS program, experts say, threatens many crucial chemicals used by a variety of industries. A new IRIS assessment finding that a specific chemical that’s been in use for years is carcinogenic, for instance, could hamper industries that rely on that chemical if the EPA decides to pass new regulation. Chemical companies and lobbying groups have waged a long battle against the IRIS program, using various tactics—including introducing opposing research produced by paid consulting groups—to downplay the program’s findings and delay assessments. In 2018, for instance, The Intercept reported that an environmental consulting company that counts chemical giants among its clients challenged an IRIS assessment of chloroprene, a chemical used in rubber production. The program was forced to use resources and staff time putting together an extensive response defending its analysis.
“‘Hate the policy, attack the science’ became a strategy for many major industries,” says Burke. “They learned that the delay game of attacking the science led to the delay of implementing regulation.”
President Donald Trump’s first administration also tried to attack IRIS. A 2018 Senate appropriations bill suggested eliminating IRIS’s independence by folding it into another program within the EPA. IRIS also faced challenges from new leadership inside the EPA, including Nancy Beck, a former policy director at the American Chemistry Council (ACC), the main lobbying arm for the chemical industry, who oversaw the EPA’s office of chemical regulation between 2017 and 2020. Yet Congress eventually chose to fund the program that year, and the general structure of IRIS survived past the first Trump administration.
But with such a long track record of opposition—and with Trump’s second administration ripping up entire agencies—it’s perhaps unsurprising that IRIS is on the chopping block now. The program was singled out twice in Project 2025. IRIS has also been attacked by legislation introduced in Congress this session, called the No IRIS Act. A press release for the House bill quotes the CEO of ACC, who also authored an op-ed in the Washington Examiner in March calling on the agency to eliminate the program.
In a separate press release issued last week, the ACC lauded EPA administrator Lee Zeldin’s choice to reorganize the agency. While the EPA has made no public comment about the future of the IRIS program, the press release devotes two paragraphs to IRIS, claiming that the program’s assessments “jeopardize access to critical chemistries, undercut national priorities, and harm American competitiveness,” while asserting the ACC’s support for the No IRIS Act.
“The IRIS program has never been authorized by Congress, and since 2009 the program has remained on the [Government Accountability Office’s] High-Risk List, which identifies government programs that are vulnerable to fraud, waste, abuse, or mismanagement,” the ACC press release states. But in the original High-Risk List addition in 2009, the GAO stated that it added IRIS not over concerns of fraud or abuse, but because the program was not working through analyses of harmful chemicals fast enough to protect the public. “Some of the IRIS assessments that have been in progress the longest cover key chemicals likely to cause cancer or other significant health effects,” the 2009 listing states. Several reforms since then, the GAO report states, have improved the program. GAO’s current critiques of IRIS, updated in 2025, focus mainly around a lack of staff and budget needed to speed up reviews.
Tom Flanagin, a spokesperson from the American Chemistry Council, told WIRED in an email that the group believes “the IRIS program should be disbanded and the responsibilities of the program should be returned to the program offices” and that Congress should pass the No IRIS Act.
“IRIS assessments jeopardize access to critical chemistries, undercut national priorities, and harm American competitiveness,” Flanagin added.
If IRIS is eliminated, experts say, EPA research on toxic chemicals will continue—but the work will likely be siloed to offices dealing with specific aspects of the environment. Instead of a central body coordinating independent reviews, individual offices will have to do more targeted assessments of chemical impacts.
“If Office of Water wants to look at a chemical like arsenic, and the [Office of Air and Radiation] is also looking at arsenic, and Superfund is also looking at arsenic—they could come up with different numbers, and that could set up a vulnerability for the agency,” says Orme-Zavaleta.
Research on chemicals will now also be loaded onto a reduced workforce of scientists working under an administration with new priorities. While significantly slashing the agency’s budget, Zeldin has said he intends to put EPA staff to work clearing the backlog of new industrial chemicals and pesticides awaiting approval in the Office of Chemical Safety and Pollution Prevention. That office is now headed, once again, by Beck, the former ACC policy director, who helped rewrite rules making it more difficult to track the health consequences of certain forever chemicals during her first tenure at the EPA.
“Your attack on Dr. Beck is insulting and unfounded,” Vaseliou, the EPA spokesperson, told WIRED. “This is yet another example of false accusations that left propaganda also known as media take as gospel. It’s fascinating that the liberal media continues to mischaracterize Dr. Beck’s time at ACC, fails to mention her time as a career civil servant (at both the state and federal level for over a decade) and fails to mention that she was a Science and Technology Policy Fellow with the American Association for the Advancement of Science for two years, a program that is typically considered to be highly competitive and highly regarded.”
“As she has done her entire career, Dr. Beck remains committed to being led by the science, unlike Biden EPA appointees with major ethical issues that were beholden to radical stakeholder groups,” Vaseliou added.
Regardless of how research is reorganized moving forward, experts say that the mass of scientists being forced out of the agency will slow down any future regulation of chemicals.
“Nothing is getting regulated right now,” says Orme-Zavaleta. “Reorganization takes a lot of time. They’re here for a four-year stint, and not much is going to happen other than rollbacks. That’s part of the strategy: Have people leave, and upend things so much that nothing is getting done.”
4 notes
·
View notes
Text
Pegasus 1.2: High-Performance Video Language Model

Pegasus 1.2 revolutionises long-form video AI with high accuracy and low latency. Scalable video querying is supported by this commercial tool.
TwelveLabs and Amazon Web Services (AWS) announced that Amazon Bedrock will soon provide Marengo and Pegasus, TwelveLabs' cutting-edge multimodal foundation models. Amazon Bedrock, a managed service, lets developers access top AI models from leading organisations via a single API. With seamless access to TwelveLabs' comprehensive video comprehension capabilities, developers and companies can revolutionise how they search for, assess, and derive insights from video content using AWS's security, privacy, and performance. TwelveLabs models were initially offered by AWS.
Introducing Pegasus 1.2
Unlike many academic contexts, real-world video applications face two challenges:
Real-world videos might be seconds or hours lengthy.
Proper temporal understanding is needed.
TwelveLabs is announcing Pegasus 1.2, a substantial industry-grade video language model upgrade, to meet commercial demands. Pegasus 1.2 interprets long films at cutting-edge levels. With low latency, low cost, and best-in-class accuracy, model can handle hour-long videos. Their embedded storage ingeniously caches movies, making it faster and cheaper to query the same film repeatedly.
Pegasus 1.2 is a cutting-edge technology that delivers corporate value through its intelligent, focused system architecture and excels in production-grade video processing pipelines.
Superior video language model for extended videos
Business requires handling long films, yet processing time and time-to-value are important concerns. As input films increase longer, a standard video processing/inference system cannot handle orders of magnitude more frames, making it unsuitable for general adoption and commercial use. A commercial system must also answer input prompts and enquiries accurately across larger time periods.
Latency
To evaluate Pegasus 1.2's speed, it compares time-to-first-token (TTFT) for 3–60-minute videos utilising frontier model APIs GPT-4o and Gemini 1.5 Pro. Pegasus 1.2 consistently displays time-to-first-token latency for films up to 15 minutes and responds faster to lengthier material because to its video-focused model design and optimised inference engine.
Performance
Pegasus 1.2 is compared to frontier model APIs using VideoMME-Long, a subset of Video-MME that contains films longer than 30 minutes. Pegasus 1.2 excels above all flagship APIs, displaying cutting-edge performance.
Pricing
Cost Pegasus 1.2 provides best-in-class commercial video processing at low cost. TwelveLabs focusses on long videos and accurate temporal information rather than everything. Its highly optimised system performs well at a competitive price with a focused approach.
Better still, system can generate many video-to-text without costing much. Pegasus 1.2 produces rich video embeddings from indexed movies and saves them in the database for future API queries, allowing clients to build continually at little cost. Google Gemini 1.5 Pro's cache cost is $4.5 per hour of storage, or 1 million tokens, which is around the token count for an hour of video. However, integrated storage costs $0.09 per video hour per month, x36,000 less. Concept benefits customers with large video archives that need to understand everything cheaply.
Model Overview & Limitations
Architecture
Pegasus 1.2's encoder-decoder architecture for video understanding includes a video encoder, tokeniser, and big language model. Though efficient, its design allows for full textual and visual data analysis.
These pieces provide a cohesive system that can understand long-term contextual information and fine-grained specifics. It architecture illustrates that tiny models may interpret video by making careful design decisions and solving fundamental multimodal processing difficulties creatively.
Restrictions
Safety and bias
Pegasus 1.2 contains safety protections, but like any AI model, it might produce objectionable or hazardous material without enough oversight and control. Video foundation model safety and ethics are being studied. It will provide a complete assessment and ethics report after more testing and input.
Hallucinations
Occasionally, Pegasus 1.2 may produce incorrect findings. Despite advances since Pegasus 1.1 to reduce hallucinations, users should be aware of this constraint, especially for precise and factual tasks.
#technology#technews#govindhtech#news#technologynews#AI#artificial intelligence#Pegasus 1.2#TwelveLabs#Amazon Bedrock#Gemini 1.5 Pro#multimodal#API
2 notes
·
View notes
Text
Been playing Mass Effect lately and have to say it's so interesting how paragon Shepard is the definition of a "good cop". You're upholding a racially hierarchical regime where some aliens are explicitly stated to be seen as lesser and incapable of self governance despite being literal spacefarers with their own personal governments, and the actual emphasized incompetence of those supposedly "capable of governing", the council allows for all sorts of excesses and brutality among it's guard seemingly, and chooses on whims whether or not to aid certain species in their struggles based on favoritism, there is, from the councils perspective, *literal* slave labor used on the citadel that they're indifferent to because again, lesser species (they don't know that the keepers are designed to upkeep the citadel they just see them as an alien race to take advantage of at 0 cost), there is seemingly overt misogyny present among most races that is in no way tackled or challenged, limitations on free speech, genocide apologia from the highest ranks and engrained into educational databases, and throughout all of this, Shepard can't offer any institutional critique, despite being the good guy hero jesus person, because she's incapable of analyzing the system she exists in and actively serves and furthers. sure she criticizes individual actions of the council and can be rude to them, but ultimately she remains beholden to them, and carries out their missions, choosing to resolve them as a good cop or bad cop, which again maybe individually means saving a life or committing police brutality, but she still ultimately reinforces a system built upon extremely blatant oppression and never seriously questions this, not even when she leaves and joins Cerberus briefly.
And then there's the crew, barring Liara (who incidentally is the crewmate least linked to the military, and who,, is less excluded from this list in ME2,, but i wanna focus on 1) Mass Effect 1 feels like Bad Apple fixer simulator, you start with
Garrus: genocide apologist (thinks the genophage was justified) who LOVES extrajudicial murder
Ashley: groomed into being a would-be klan member
Tali: zionist who hated AI before it was cool (in a genocidal way)
Wrex: war culture mercenary super chill on war crimes
Kaidan: shown as the other "good cop" and generally the most reasonable person barring Liara, but also he did just murder someone in boot camp in a fit of rage
Through your actions, you can fix them! You can make the bad apples good apples (kinda) but like,,,,
2 of course moves away from this theme a bit while still never properly tackling corrupt institutions in a way that undoes the actions of the first game, but its focus is elsewhere and the crew is more diverse in its outlook
Ultimately i just find it interesting how Mass Effect is a game showcasing how a good apple or whatever is capable of making individual changes for the better but is ultimately still a tool of an oppressive system and can't do anything to fundamentally change that, even if they're the most important good apple in said system.
Worth noting maybe this'll change in Mass Effect 3, which i have yet to play as im in the process of finishing 2 currently (im a dragon age girl) but idk i like how it's handled at first i was iffy on it but no it's actually pretty cool.
Also sorry if this is super retreaded ground im new to mass effect discourse this is just my takeaways from it lol
18 notes
·
View notes
Text
My Experience with Database Homework Help from DatabaseHomeworkHelp.com
As a student majoring in computer science, managing the workload can be daunting. One of the most challenging aspects of my coursework has been database management. Understanding the intricacies of SQL, ER diagrams, normalization, and other database concepts often left me overwhelmed. That was until I discovered Database Homework Help from DatabaseHomeworkHelp.com. This service has been a lifesaver, providing me with the support and guidance I needed to excel in my studies.
The Initial Struggle
When I first started my database course, I underestimated the complexity of the subject. I thought it would be as straightforward as other programming courses I had taken. However, as the semester progressed, I found myself struggling with assignments and projects. My grades were slipping, and my confidence was waning. I knew I needed help, but I wasn't sure where to turn.
I tried getting assistance from my professors during office hours, but with so many students needing help, the time available was limited. Study groups with classmates were somewhat helpful, but they often turned into social gatherings rather than focused study sessions. I needed a more reliable and structured form of support.
Discovering DatabaseHomeworkHelp.com
One evening, while frantically searching for online resources to understand an especially tricky ER diagram assignment, I stumbled upon DatabaseHomeworkHelp.com. The website promised expert help on a wide range of database topics, from basic queries to advanced database design and implementation. Skeptical but hopeful, I decided to give it a try. It turned out to be one of the best decisions I’ve made in my academic career.
First Impressions
The first thing that struck me about DatabaseHomeworkHelp.com was the user-friendly interface. The website was easy to navigate, and I quickly found the section where I could submit my assignment. The process was straightforward: I filled out a form detailing my assignment requirements, attached the relevant files, and specified the deadline.
Within a few hours, I received a response from one of their database experts. The communication was professional and reassuring. They asked a few clarifying questions to ensure they fully understood my needs, which gave me confidence that I was in good hands.
The Quality of Help
What impressed me the most was the quality of the assistance I received. The expert assigned to my task not only completed the assignment perfectly but also provided a detailed explanation of the solutions. This was incredibly helpful because it allowed me to understand the concepts rather than just submitting the work.
For example, in one of my assignments, I had to design a complex database schema. The expert not only provided a well-structured schema but also explained the reasoning behind each table and relationship. This level of detail helped me grasp the fundamental principles of database design, something I had been struggling with for weeks.
Learning and Improvement
With each assignment I submitted, I noticed a significant improvement in my understanding of database concepts. The experts at DatabaseHomeworkHelp.com were not just solving problems for me; they were teaching me how to solve them myself. They broke down complex topics into manageable parts and provided clear, concise explanations.
I particularly appreciated their help with SQL queries. Writing efficient and effective SQL queries was one of the areas I found most challenging. The expert guidance I received helped me understand how to approach query writing logically. They showed me how to optimize queries for better performance and how to avoid common pitfalls.
Timely Delivery
Another aspect that stood out was their commitment to deadlines. As a student, timely submission of assignments is crucial. DatabaseHomeworkHelp.com always delivered my assignments well before the deadline, giving me ample time to review the work and ask any follow-up questions. This reliability was a significant relief, especially during times when I had multiple assignments due simultaneously.
Customer Support
The customer support team at DatabaseHomeworkHelp.com deserves a special mention. They were available 24/7, and I never had to wait long for a response. Whether I had a question about the pricing, needed to clarify the assignment details, or required an update on the progress, the support team was always there to assist me promptly and courteously.
Affordable and Worth Every Penny
As a student, budget is always a concern. I was worried that professional homework help would be prohibitively expensive. However, I found the pricing at DatabaseHomeworkHelp.com to be reasonable and affordable. They offer different pricing plans based on the complexity and urgency of the assignment, making it accessible for students with varying budgets.
Moreover, considering the quality of help I received and the improvement in my grades, I can confidently say that their service is worth every penny. The value I got from their expert assistance far outweighed the cost.
A Lasting Impact
Thanks to DatabaseHomeworkHelp.com, my grades in the database course improved significantly. But beyond the grades, the most valuable takeaway has been the knowledge and confidence I gained. I now approach database assignments with a clearer understanding and a more structured method. This confidence has also positively impacted other areas of my studies, as I am less stressed and more organized.
Final Thoughts
If you're a student struggling with database management assignments, I highly recommend Database Homework Help from DatabaseHomeworkHelp.com. Their expert guidance, timely delivery, and excellent customer support can make a significant difference in your academic journey. They don’t just provide answers; they help you understand the material, which is crucial for long-term success.
In conclusion, my experience with DatabaseHomeworkHelp.com has been overwhelmingly positive. The support I received has not only helped me improve my grades but also enhanced my overall understanding of database concepts. I am grateful for their assistance and will undoubtedly continue to use their services as I progress through my computer science degree.

7 notes
·
View notes
Text
mmo rp is kind of fundamentally not so different from RPing in any messaging program, something we've been doing since the days of IRC. the story you co-create is primarily driven by what's written in the text box. no matter how well made the emote animations are, they are not communicative enough to really tell a complex story, so you always fall back to prose. your character's voice will be limited to a handful of nonverbal expressions - a laugh, mm-hm, uh-huh. you are constantly having to reinterpret bits of game jank as you construct your mental version of the 'real story'. and yet
these visual aids do make a really substantial difference in how you experience it i think. to honestly a kind of surprising degree. of course having a character design on screen helps avoid writing tons of descriptive prose - but there's also a lot that can be done with simple movement through space, like a character positioning themselves besides another, retreating to sulk, getting up to dance.
like in visual novels and manga, you have essentially a set of codified, symbolic expressions - but in FFXIV, every race has its own set of very charming and polished animations for nearly every emote, which adds a huge amount of info in how you interpret that character (and slot them into the otaku database). a roegadyn will by default be loud and brash, a viera refined and dreamy, a lala mischievous and childlike. a mi'qote is a cat. since all of these are chosen by the player, they act as a strong signal of what your character's deal is - their body language comes across even if it's not like the actual scene fully acted out.
and what's fascinating to me is that even when i know what the player looks like irl, i still find myself responding to their game embodiment in how i think about them, i don't picture them irl... but also, having the embodiment helps me get into character. I have two alts, and with each one i feel drawn to a different style of roleplay. just like a list of prompts in a ttrpg sourcebook, the embodiment you've chosen gives you something to bounce off when you're improvising.
roleplaying is very similar to improv comedy, and many of the same analysis concepts - 'offers', 'yes, and' - apply. we're essentially improvising a digital puppet show. building up an RP venue and customising our model is a way of laying out props to help that process roll smoothly.
i often dream about an mmo animation system that would be less janky - more control over camera placement, better handling of interactions between player characters and characters with their environment, more ability to plan out timing and blocking and so on - essentially trending towards multiplayer source filmmaker.
the problem is that such a system would probably have way too much cognitive overhead to be usable in real time improv. i think what something like ffxiv shows is that even very simple elements - besides the emotes, your character looks towards your target and moves their lips when you talk, you can adjust their expression and there's animation hooks all over the place line chairs you can sit on - can actually be a very expressive palette and people are pretty good at filtering out the jank when they want to create a story together.
indeed, it becomes a skill - knowing what animations you have, how to reinterpret them, how to line yourself up with other players. and in the end you don't remember the time spent shuffling forwards and typing /hug again and again, or standing up and sitting down repeatedly until it lines up right. you remember the cute sight of your character sitting beside your friend, looking fondly at each other.
there's also another angle which is like... i find real life 'going out' very difficult - usually hitting a point of information overload very quickly in a pub environment, and while music is easier to manage than a wall of conversation, i never really learned how to interact with strangers at a club, concert, convention. I'm not good with alcohol. when i try to a pub, i usually end up retreating into myself and ducking out. in mmos, though... i find prose much more easy to be expressive in, and the limits of the animation system kind of level the playing field a bit in terms of The Autism when it comes to body language and the like.
still, sometimes it feels like a very sad existence - i rely on this simulacrum, pretending i am being intimate and social with people i can't touch through a computer program that draws triangles. everything in an mmo is muted, blunted by the medium - which makes it 'safe', but also tinges it with a loneliness that can't really be broken. but for now, i guess the simulacrum is all I've got, you know? and i can appreciate how it's put together, all the effort that has gone in from devs and players alike to realise this alternative channel for connection.
but yeah. i guess it comes back to this again... there's a reason my online 'face' is a low poly approximation of an animal!
#roleplaying games#that said i should totally check out vrchat again now i have the gear lol#computer games#mmorpgs#ffxiv#introspective nightposting
18 notes
·
View notes
Text
All about fundamentals of website design and development – A beginner’s handbook

As we all know in today’s world everyone is using websites, apps, social media platforms etc. regularly. Knowing and understanding the fundamentals of website design and development is the first step towards your website journey. We need to understand the basic things behind all these website designs, apps and platforms. There are multiple aspects to be considered in creating a website.
Have you ever came across any website and felt its very user friendly, looks great.
Have you ever thought how these websites will be designed and developed. What kind of design software they use in website designing process?
As a business owner, knowledge on website design and development is a must nowadays. This knowledge give you idea how to market your products or services in a better way.
If you are looking to learn basic of website design or confused with different concepts , this blog is one stop solution for all your learning needs.
In this beginner’s handbook we will cover all the crucial components of web design and development and also highlights key aspects to be considered when looking for the best website design and development agency in India. You can reach out to us as we are the well known website design and development company in Bangalore.
In this article we can cover all about web design and its role in business growth.
What is web design?
It is a part of website design and development includes website layout, colors , typography, user interface and other visual aspects. Web design is crucial as it makes website looks visually appealing, engaging and user friendly.
Web designer is a professional who has a skill of designing websites. Web designer must understand the website’s purpose, visual elements and the target audience.
Web designing is a creative process in which graphic designer creates a visual elements to integrate in the website.
What is website development?
Website development involves technical side of building a Website. It includes coding, server configuration, database management, and make sure the website functions as needed.
Several programming languages are used to convert a web design to a functioning website during the website development process. HTML and CSS are the most popular languages used to design a web pages.
Web developer is a professional who has the skills to develop websites.
Importance of a website in business:
A well designed website assist in multiple purposes such as
First impressions: First impression always create a long lasting impact so as the first impression of any visitors is crucial. A great web design builds trust and encourages users to explore more.
User experience(UX): Good design increases usability which helps to navigate the site and find information.
Search Engine Optimization: Web design integrates SEO best practices, by making sure that the website ranks well in search engines and improving visibility.
Conversion rates: A visually appealing and navigational website increases the rate of conversion, by transforming visitors into customers.
Key elements of Website Design
Layout:
Layout represents how a content is organized in webpage. A good layout gets user attention and will be easier to process information. Most used layout styles are:
Grid layout: This layout style uses grid system to structure content, offering a well organized look.
F-shape layout: This layout helps in enhancing usability as in this design elements align with the reading behavior. Some studies shows that users read in F- pattern.
Color scheme:
Colors evoke emotions by influencing user behavior. Factors to be considered while choosing color:
Brand identity: Select colors that reflects your brand identity
Contrast: Make sure there is contrast variation between text and background to make it readable.
Typography :
Typography has a huge impact on readability and user experience. Consider factors like:
Fonts: Use fonts that are easy to read and to maintain a cohesive look.
Hierarchy: Create a visual hierarchy by using proper size and weight making users to find the important information.
Images and graphics:
Visual elements such as images, videos , graphics and icons helps in improving website appeal. Make sure you work on factors like:
Quality: Use relevant high resolution images that matches with your content.
Loading speed: Optimize images for fast loading speed , as speed plays a major role in improving user experience and SEO
Navigation:
Having a well structured navigation is vital for better usability. Consider the following to achieve it:
Simplicity: Make sure navigation is simple
Accessibility: Ensure your website is accessible on all devices including mobile
Fundamentals of web development:
Front end development:
It refers to everything a user see and interact with website. It includes:
HTML(Hypertext Markup Language) : HTML helps in structuring the content as It is a pillar of webpages.
CSS (Cascading Style Sheets) : It adds styles to HTML, layout , colors and fonts.
Java script : This is a programming language which make web pages interactive, making user experience better.
Back end development:
It focuses on server side functionality. It includes:
Server: It is a place where website’s files and data is stored. Server process requests and serves the web pages to users.
Database: Helps to store and manage data. One of the popular database is MySQL
Server-side languages: We can use languages such as PHP or python for communication between server and database.
Content Management Systems (CMS):
CMS allows users to create the digital content and manage it effortlessly. Most used CMS platform by beginners include WordPress as it is highly user friendly and customizable
Factors to consider when choosing web design and development agency:
When looking for the web design and development agency in India , follow these tips:
Review the agency’s portfolio to understand their work style and capability. Check for their various projects or clients handled which matches with your business style and vision
Check for previous clients reviews , ratings and testimonials . If there is a positive feedback then you can consider that agency.
Go through the list of services the agency offers such as web design , development , SEO , Digital Marketing and Branding.
Consider a agency which maintains transparent communication by being open to any kind of feedback and ready to collaborate and support regularly throughout the project.
We should always choose an agency that fits your budget. Get quotes, compare their services and pricing and finalize the agency that suits you best.
Why choose Synwolf as a web design and development agency?
When it comes to the best agency for web design and development , Synwolf stands high in competition as a premier choice for businesses who are looking for designing a website to take their business next level. We have a team who are creative as well as having technical expertise to design a website as per your business goals. We mainly focus on understanding your business, goals to make sure every aspect of your website from layout to functionality aligns with your vision. By prioritizing user experience we integrate eye catchy visuals that helps in getting engagement and more conversions. We maintain transparent communication over a period of designing website which allows you to collaborate with us and assist us on getting your dream website designed without any flaws and meets your expectations. Contact us today to start your journey of business growth in this online world.
Conclusion:
Understanding the basics and fundamentals included in website design and development is very essential in this digital age. Focusing on key elements like layout, color, typography and navigation you can enhance user experience. Building knowledge on these aspects helps you to navigate the world of web design and development with confidence. Whether you are creating a personal blog, e-commerce site, corporate platform or looking for a professional assistance this handbook will help in laying a foundation for your business success. If you are looking for a professional help from website design and development company make an informed decisions based on your requirements and their expertise.
Today the entire world is becoming digitalized. Most of the people spends time online for all kind of activities. Websites has become common and takes center stage in this time. We can access any kind of information at our fingertips with a website. If a company does not have a user friendly website then it going to losing most of its customers. As a business its mandatory to you to have a well designed and user friendly website. For that you need a very good and well known web design and development services in India for your business growth. Contact our team today.
#website design and development#website#web design#web development#website design#wordpress#digital marketing services#web desgin company#web developing company
2 notes
·
View notes
Text
Which is better full stack development or testing?

Full Stack Development vs Software Testing: Which Career Path is Right for You?
In today’s rapidly evolving IT industry, choosing the right career path can be challenging. Two popular options are Full Stack Development and Software Testing. Both of these fields offer unique opportunities and cater to different skill sets, making it essential to assess which one aligns better with your interests, goals, and long-term career aspirations.
At FirstBit Solutions, we take pride in offering a premium quality of teaching, with expert-led courses designed to provide real-world skills. Our goal is to help you know, no matter which path you choose. Whether you’re interested in development or testing, our 100% unlimited placement call guarantee ensures ample job opportunities. In this answer, we’ll explore both career paths to help you make an informed decision.
Understanding Full Stack Development
What is Full Stack Development?
Full Stack Development involves working on both the front-end (client-side) and back-end (server-side) of web applications. Full stack developers handle everything from designing the user interface (UI) to managing databases and server logic. They are versatile professionals who can oversee a project from start to finish.
Key Skills Required for Full Stack Development
To become a full stack developer, you need a diverse set of skills, including:
Front-End Technologies: HTML, CSS, and JavaScript are the fundamental building blocks of web development. Additionally, proficiency in front-end frameworks like React, Angular, or Vue.js is crucial for creating dynamic and responsive web interfaces.
Back-End Technologies: Understanding back-end programming languages like Node.js, Python, Ruby, Java, or PHP is essential for server-side development. Additionally, knowledge of frameworks like Express.js, Django, or Spring can help streamline development processes.
Databases: Full stack developers must know how to work with both SQL (e.g., MySQL, PostgreSQL) and NoSQL (e.g., MongoDB) databases.
Version Control and Collaboration: Proficiency in tools like Git, GitHub, and agile methodologies is important for working in a collaborative environment.
Job Opportunities in Full Stack Development
Full stack developers are in high demand due to their versatility. Companies often prefer professionals who can handle both front-end and back-end tasks, making them valuable assets in any development team. Full stack developers can work in:
Web Development
Mobile App Development
Enterprise Solutions
Startup Ecosystems
The flexibility to work on multiple layers of development opens doors to various career opportunities. Moreover, the continuous rise of startups and digital transformation initiatives has further fueled the demand for full stack developers.
Benefits of Choosing Full Stack Development
High Demand: The need for full stack developers is constantly increasing across industries, making it a lucrative career choice.
Versatility: You can switch between front-end and back-end tasks, giving you a holistic understanding of how applications work.
Creativity: If you enjoy creating visually appealing interfaces while also solving complex back-end problems, full stack development allows you to engage both creative and logical thinking.
Salary: Full stack developers typically enjoy competitive salaries due to their wide skill set and ability to handle various tasks.
Understanding Software Testing
What is Software Testing?
Software Testing is the process of evaluating and verifying that a software product or application is free of defects, meets specified requirements, and functions as expected. Testers ensure the quality and reliability of software by conducting both manual and automated tests.
Key Skills Required for Software Testing
To succeed in software testing, you need to develop the following skills:
Manual Testing: Knowledge of testing techniques, understanding different testing types (unit, integration, system, UAT, etc.), and the ability to write test cases are fundamental for manual testing.
Automated Testing: Proficiency in tools like Selenium, JUnit, TestNG, or Cucumber is essential for automating repetitive test scenarios and improving efficiency.
Attention to Detail: Testers must have a keen eye for identifying potential issues, bugs, and vulnerabilities in software systems.
Scripting Knowledge: Basic programming skills in languages like Java, Python, or JavaScript are necessary to write and maintain test scripts for automated testing.
Job Opportunities in Software Testing
As the demand for high-quality software increases, so does the need for skilled software testers. Companies are investing heavily in testing to ensure that their products perform optimally in the competitive market. Software testers can work in:
Manual Testing
Automated Testing
Quality Assurance (QA) Engineering
Test Automation Development
With the rise of Agile and DevOps methodologies, the role of testers has become even more critical. Continuous integration and continuous delivery (CI/CD) pipelines rely on automated testing to deliver reliable software faster.
Benefits of Choosing Software Testing
Job Security: With software quality being paramount, skilled testers are in high demand, and the need for testing professionals will only continue to grow.
Quality Assurance: If you have a knack for perfection and enjoy ensuring that software works flawlessly, testing could be a satisfying career.
Automated Testing Growth: The shift toward automation opens up new opportunities for testers to specialize in test automation tools and frameworks, which are essential for faster releases.
Flexibility: Testing provides opportunities to work across different domains and industries, as almost every software product requires thorough testing.
Full Stack Development vs Software Testing: A Comparative Analysis
Let’s break down the major factors that could influence your decision:
Factors
Full Stack Development
Software Testing
Skills
Proficiency in front-end and back-end technologies, databases
Manual and automated testing, attention to detail, scripting
Creativity
High – involves creating and designing both UI and logic
Moderate – focuses on improving software through testing and validation
Job Roles
Web Developer, Full Stack Engineer, Mobile App Developer
QA Engineer, Test Automation Engineer, Software Tester
Career Growth
Opportunities to transition into senior roles like CTO or Solution Architect
Growth towards roles in automation and quality management
Salary
Competitive with wide-ranging opportunities
Competitive, with automation testers in higher demand
Demand
High demand due to increasing digitalization and web-based applications
Consistently high, especially in Agile/DevOps environments
Learning Curve
Steep – requires mastering multiple languages and technologies
Moderate – requires a focus on testing tools, techniques, and automation
Why Choose FirstBit Solutions for Full Stack Development or Software Testing?
At FirstBit Solutions, we provide comprehensive training in both full stack development and software testing. Our experienced faculty ensures that you gain hands-on experience and practical knowledge in the field of your choice. Our 100% unlimited placement call guarantee ensures that you have ample opportunities to land your dream job, no matter which course you pursue. Here’s why FirstBit is your ideal training partner:
Expert Trainers: Learn from industry veterans with years of experience in development and testing.
Real-World Projects: Work on real-world projects that simulate industry scenarios, providing you with the practical experience needed to excel.
Job Assistance: Our robust placement support ensures you have access to job openings with top companies.
Flexible Learning: Choose from online and offline batch options to fit your schedule.
Conclusion: Which Career Path is Right for You?
Ultimately, the choice between full stack development and software testing comes down to your personal interests, skills, and career aspirations. If you’re someone who enjoys building applications from the ground up, full stack development might be the perfect fit for you. On the other hand, if you take satisfaction in ensuring that software is of the highest quality, software testing could be your calling.
At FirstBit Solutions, we provide top-notch training in both fields, allowing you to pursue your passion and build a successful career in the IT industry. With our industry-aligned curriculum, expert guidance, and 100% placement call guarantee, your future is in good hands.
So, what are you waiting for? Choose the course that excites you and start your journey toward a rewarding career today!
#education#programming#tech#technology#training#python#full stack developer#software testing#itservices#java#.net#.net developers#datascience
2 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
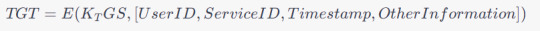
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text
Business Potential with Advanced Data Engineering Solutions
In the age of information, businesses are swamped with data. The key to turning this data into valuable insights lies in effective data engineering. Advanced data engineering solutions help organizations harness their data to drive better decisions and outcomes.
Why Data Engineering Matters
Data engineering is fundamental to making sense of the vast amounts of data companies collect. It involves building and maintaining the systems needed to gather, store, and analyze data. With the right data engineering solutions, businesses can manage complex data environments and ensure their data is accurate and ready for analysis.
1. Seamless Data Integration and Transformation
Handling data from various sources—like databases, cloud services, and third-party apps—can be challenging. Data engineering services streamline this process by integrating and transforming data into a unified format. This includes extracting data, cleaning it, and making it ready for in-depth analysis.
2. Efficient Data Pipeline Development
Data pipelines automate the flow of information from its source to its destination. Reliable and scalable pipelines can handle large volumes of data, ensuring continuous updates and availability. This leads to quicker and more informed business decisions.
3. Centralized Data Warehousing
A data warehouse serves as a central repository for storing data from multiple sources. State-of-the-art data warehousing solutions keep data organized and accessible, improving data management and boosting the efficiency of analysis and reporting.
4. Ensuring Data Quality and Governance
For accurate analytics, maintaining high data quality is crucial. Rigorous data validation and cleansing processes, coupled with strong governance frameworks, ensure that data remains reliable, compliant with regulations, and aligned with best practices. This fosters confidence in business decisions.
5. Scalable and Adaptable Solutions
As businesses grow, their data needs evolve. Scalable data engineering solutions can expand and adapt to changing requirements. Whether dealing with more data or new sources, these solutions are designed to keep pace with business growth.
The Advantages of Working with a Data Engineering Expert
Teaming up with experts in data engineering offers several key benefits:
1. Expertise You Can Rely On
With extensive experience in data engineering, professionals bring a high level of expertise to the table. Their team is adept at the latest technologies and practices, ensuring businesses receive top-notch solutions tailored to their needs.
2. Tailored Solutions
Every business has unique data challenges. Customized data engineering solutions are designed to meet specific requirements, ensuring you get the most out of your data investments.
3. Cutting-Edge Technology
Leveraging the latest technologies and tools ensures innovative data engineering solutions that keep you ahead of the curve. This commitment to technology provides effective data management and analytics practices.
4. Improved Data Accessibility and Insights
Advanced data engineering solutions enhance how you access and interpret your data. By streamlining processes like data integration and storage, they make it easier to generate actionable insights and make informed decisions.
Conclusion
In a world where data is a critical asset, having robust data engineering solutions is essential for maximizing its value. Comprehensive services that cover all aspects of data engineering—from integration and pipeline development to warehousing and quality management—can transform your data practices, improve accessibility, and unlock powerful insights that drive your business forward.
5 notes
·
View notes
Text
From Beginner to Pro: A Game-Changing Big Data Analytics Course
Are you fascinated by the vast potential of big data analytics? Do you want to unlock its power and become a proficient professional in this rapidly evolving field? Look no further! In this article, we will take you on a journey to traverse the path from being a beginner to becoming a pro in big data analytics. We will guide you through a game-changing course designed to provide you with the necessary information and education to master the art of analyzing and deriving valuable insights from large and complex data sets.

Step 1: Understanding the Basics of Big Data Analytics
Before diving into the intricacies of big data analytics, it is crucial to grasp its fundamental concepts and methodologies. A solid foundation in the basics will empower you to navigate through the complexities of this domain with confidence. In this initial phase of the course, you will learn:
The definition and characteristics of big data
The importance and impact of big data analytics in various industries
The key components and architecture of a big data analytics system
The different types of data and their relevance in analytics
The ethical considerations and challenges associated with big data analytics
By comprehending these key concepts, you will be equipped with the essential knowledge needed to kickstart your journey towards proficiency.
Step 2: Mastering Data Collection and Storage Techniques
Once you have a firm grasp on the basics, it's time to dive deeper and explore the art of collecting and storing big data effectively. In this phase of the course, you will delve into:
Data acquisition strategies, including batch processing and real-time streaming
Techniques for data cleansing, preprocessing, and transformation to ensure data quality and consistency
Storage technologies, such as Hadoop Distributed File System (HDFS) and NoSQL databases, and their suitability for different types of data
Understanding data governance, privacy, and security measures to handle sensitive data in compliance with regulations
By honing these skills, you will be well-prepared to handle large and diverse data sets efficiently, which is a crucial step towards becoming a pro in big data analytics.
Step 3: Exploring Advanced Data Analysis Techniques
Now that you have developed a solid foundation and acquired the necessary skills for data collection and storage, it's time to unleash the power of advanced data analysis techniques. In this phase of the course, you will dive into:
Statistical analysis methods, including hypothesis testing, regression analysis, and cluster analysis, to uncover patterns and relationships within data
Machine learning algorithms, such as decision trees, random forests, and neural networks, for predictive modeling and pattern recognition
Natural Language Processing (NLP) techniques to analyze and derive insights from unstructured text data
Data visualization techniques, ranging from basic charts to interactive dashboards, to effectively communicate data-driven insights
By mastering these advanced techniques, you will be able to extract meaningful insights and actionable recommendations from complex data sets, transforming you into a true big data analytics professional.
Step 4: Real-world Applications and Case Studies
To solidify your learning and gain practical experience, it is crucial to apply your newfound knowledge in real-world scenarios. In this final phase of the course, you will:
Explore various industry-specific case studies, showcasing how big data analytics has revolutionized sectors like healthcare, finance, marketing, and cybersecurity
Work on hands-on projects, where you will solve data-driven problems by applying the techniques and methodologies learned throughout the course
Collaborate with peers and industry experts through interactive discussions and forums to exchange insights and best practices
Stay updated with the latest trends and advancements in big data analytics, ensuring your knowledge remains up-to-date in this rapidly evolving field
By immersing yourself in practical applications and real-world challenges, you will not only gain valuable experience but also hone your problem-solving skills, making you a well-rounded big data analytics professional.

Through a comprehensive and game-changing course at ACTE institute, you can gain the necessary information and education to navigate the complexities of this field. By understanding the basics, mastering data collection and storage techniques, exploring advanced data analysis methods, and applying your knowledge in real-world scenarios, you have transformed into a proficient professional capable of extracting valuable insights from big data.
Remember, the world of big data analytics is ever-evolving, with new challenges and opportunities emerging each day. Stay curious, seek continuous learning, and embrace the exciting journey ahead as you unlock the limitless potential of big data analytics.
17 notes
·
View notes
Text
Mastering Web Development: A Comprehensive Guide for Beginners
In the vast landscape of technology, web development stands as a crucial cornerstone. It encompasses the art and science of building websites, ranging from simple static pages to complex web applications. Whether you're aiming to pursue a career in software development or seeking to enhance your digital presence, understanding web development is essential.
In this comprehensive guide, we'll take you through the fundamental concepts and practical skills needed to master web development from scratch. Let's dive in!
1. Understanding HTML (Hypertext Markup Language)
HTML serves as the backbone of every web page, providing the structure and content. It uses tags to define different elements such as headings, paragraphs, images, and links. By mastering HTML, you'll be able to create well-structured and semantically meaningful web documents.
2. Exploring CSS (Cascading Style Sheets)
CSS is the language used to style HTML elements, enhancing their appearance and layout. With CSS, you can customize colors, fonts, spacing, and more, giving your website a polished and professional look. Understanding CSS selectors and properties is essential for effective styling.
3. Introduction to JavaScript
JavaScript is a versatile programming language that adds interactivity and dynamic behavior to web pages. From simple animations to complex web applications, JavaScript powers a wide range of functionalities. Learning JavaScript fundamentals such as variables, functions, and events is crucial for web development.
4. Building Responsive Websites
In today's mobile-centric world, it's essential to create websites that adapt seamlessly to various screen sizes and devices. Responsive web design achieves this by using fluid grids, flexible images, and media queries. Mastering responsive design principles ensures that your websites look great on desktops, tablets, and smartphones.
5. Introduction to Version Control with Git
Git is a powerful tool for tracking changes in your codebase and collaborating with other developers. By learning Git basics such as branching, merging, and committing, you can streamline your development workflow and effectively manage project versions.
6. Introduction to Front-End Frameworks
Front-end frameworks like Bootstrap, Foundation, and Materialise provide pre-designed components and stylesheets to expedite web development. By leveraging these frameworks, you can create responsive and visually appealing websites with less effort and code.
7. Introduction to Back-End Development
While front-end development focuses on the user interface, back-end development deals with server-side logic and database management. Learning back-end languages such as Node.js, Python, or PHP enables you to build dynamic web applications and handle user interactions efficiently.
8. Deploying Your Website
Once you've developed your website, it's time to make it accessible to the world. Deploying a website involves selecting a web hosting provider, uploading your files, and configuring domain settings. Understanding the deployment process ensures that your website goes live smoothly.
9. Conclusion and Next Steps
Congratulations on completing this comprehensive guide to mastering web development! By now, you've gained a solid understanding of HTML, CSS, JavaScript, version control, frameworks, and deployment. As you continue your journey in web development, remember to stay curious, practice regularly, and explore advanced topics to further refine your skills.
Resources for Further Learning:
Online tutorials and documentation
Interactive coding platforms
Community forums and discussion groups
Next Steps:
Explore advanced topics such as web performance optimization, server-side rendering, and progressive web apps.
Build real-world projects to apply your skills and showcase your portfolio.
Stay updated with the latest trends and technologies in web development through blogs, podcasts, and conferences.
With dedication and perseverance, you'll continue to evolve as a proficient web developer, creating innovative solutions and contributing to the ever-changing digital landscape . Happy coding!
4 notes
·
View notes
Text
Unveiling Expertise: An Interview with Dr. Elon, a Database Homework Help Maestro (+9 Years of Experience)
Welcome to the insightful world of database management! In our exclusive interview today, we bring you face-to-face with Dr. Elon, a seasoned expert in the realm of database homework help, boasting an impressive track record of over nine years. Dr. Elon is not just a name; it's a synonym for proficiency and passion in navigating the intricate landscapes of SQL homework assistance.
Q1: Dr. Elon, could you share a bit about your journey and what inspired you to delve into the world of database homework help?
Dr. Elon: Absolutely. My journey began with a profound interest in database systems during my academic years. As I delved deeper, I realized the challenges students faced in grasping SQL concepts. This realization ignited my passion for aiding them in mastering the art of database management.
Q2: With over nine years of experience, you've witnessed the evolution of database technology. How has this experience shaped your approach to helping students with SQL homework?
Dr. Elon: It's been an exciting ride. Over the years, I've seen technology leap forward. This experience has allowed me to adapt my teaching methods, ensuring students are not just acquainted with the fundamentals but are also well-prepared for the dynamic, real-world applications of SQL.
Q3: "Help with SQL homework" is a common plea from students. What, in your opinion, makes SQL assignments particularly challenging, and how do you assist students in overcoming these challenges?
Dr. Elon: SQL assignments often involve intricate queries and a deep understanding of database design. The challenge lies in translating theoretical knowledge into practical application. I guide students through this process, emphasizing hands-on practice and offering step-by-step assistance tailored to their learning pace.
Q4: Can you share an experience where you witnessed a student's "aha" moment while working on their SQL homework, and what strategies do you employ to foster such breakthroughs?
Dr. Elon: Oh, absolutely. There was a student struggling with a complex JOIN operation. Through patient guidance and breaking down the problem into manageable parts, the student suddenly grasped the concept. It's about building confidence through small victories and celebrating those "aha" moments.
Q5: The field of database management is ever-evolving. How do you ensure your assistance aligns with the latest trends and technologies, keeping students ahead of the curve?
Dr. Elon: Continuous learning is at the core of my approach. I stay abreast of the latest industry trends, incorporating relevant updates into my teaching materials. This ensures that students not only understand the foundational principles but are also prepared for the current demands of the field.
Conclusion:
Our interview with Dr. Elon, a stalwart in database homework help, has unveiled a wealth of experience and insights. From inspiring journeys to overcoming SQL challenges, Dr. Elon's expertise has proven instrumental in guiding students toward mastering the intricacies of database management. If you find yourself uttering the words "help with SQL homework," rest assured, Dr. Elon is the beacon of knowledge you've been seeking on your academic journey.
4 notes
·
View notes
Text
From Beginner to Expert: Mastering Java Programming
Commencing a Java learning journey involves planning, commitment, and disciplined study. In this guide, we will explore a comprehensive roadmap to effectively learn Java, equipping you with the skills and knowledge needed to become proficient in this versatile programming language.

Navigating the Path to Java Mastery:
Grasping Fundamentals: Before delving into Java, it's essential to grasp the fundamental concepts of programming. Start by familiarizing yourself with variables, data types, control structures, and basic algorithms. These foundational principles lay the groundwork for understanding Java's syntax and language features.
Setting Up Your Environment: To begin coding in Java, you'll need to set up your development environment. Install the Java Development Kit (JDK) and choose an Integrated Development Environment (IDE) such as Eclipse or IntelliJ IDEA. These tools provide essential features like syntax highlighting and debugging tools to streamline your coding experience.
Mastering Syntax and Object-Oriented Concepts: Dive into Java syntax and object-oriented programming (OOP) concepts, including classes, objects, methods, inheritance, polymorphism, encapsulation, and abstraction. Understanding these concepts is crucial for writing efficient and maintainable Java code.
Exploring Core Libraries: Java offers a robust set of core libraries that provide essential functionality for various tasks. Explore libraries such as java.lang, java.util, and java.io, which offer classes and methods for common operations like string manipulation, input/output operations, and collection manipulation.

Hands-On Practice: Practice is key to mastering Java programming. Start by writing simple programs and gradually tackle more complex challenges. Participate in coding competitions, solve coding puzzles, and work on projects to apply your knowledge in real-world scenarios.
Understanding Java APIs and Frameworks: Familiarize yourself with Java APIs and frameworks that simplify development tasks. Explore APIs for GUI development, database connectivity, web development, and more. Additionally, delve into popular Java frameworks like Spring and Hibernate, which offer reusable components and design patterns for building robust applications.
Building Projects: Project-based learning is an effective way to solidify your Java skills. Start with small projects and gradually tackle larger ones as you gain confidence. Building projects allows you to apply your knowledge in practical scenarios and enhance your problem-solving skills.
Continuous Learning and Growth: Java is a constantly evolving language, so commit to continuous learning and growth. Stay updated with the latest Java features, best practices, and industry trends. Join Java communities, attend webinars, and participate in online forums to connect with fellow developers and expand your knowledge.
Conclusion:
Mastering Java is an enriching journey that offers endless opportunities in software development. By following this roadmap, you can build a strong foundation in Java programming and unlock your full potential as a developer. Remember to stay curious, embrace challenges, and enjoy the process of learning and growing as a Java programmer. With dedication and perseverance, you can achieve proficiency in Java and embark on a fulfilling career in software development.
#java course#javascript#javaprogramming#programming#computerscience#computerengineering#programminglanguage#tech#technology#training#java training#java training course
2 notes
·
View notes
Text
The Ultimate Guide to Web Development
In today’s digital age, having a strong online presence is crucial for individuals and businesses alike. Whether you’re a seasoned developer or a newcomer to the world of coding, mastering the art of web development opens up a world of opportunities. In this comprehensive guide, we’ll delve into the intricate world of web development, exploring the fundamental concepts, tools, and techniques needed to thrive in this dynamic field. Join us on this journey as we unlock the secrets to creating stunning websites and robust web applications.
Understanding the Foundations
At the core of every successful website lies a solid foundation built upon key principles and technologies. The Ultimate Guide to Web Development begins with an exploration of HTML, CSS, and JavaScript — the building blocks of the web. HTML provides the structure, CSS adds style and aesthetics, while JavaScript injects interactivity and functionality. Together, these three languages form the backbone of web development, empowering developers to craft captivating user experiences.
Collaborating with a Software Development Company in USA
For businesses looking to build robust web applications or enhance their online presence, collaborating with a Software Development Company in USA can be invaluable. These companies offer expertise in a wide range of technologies and services, from custom software development to web design and digital marketing. By partnering with a reputable company, businesses can access the skills and resources needed to bring their vision to life and stay ahead of the competition in today’s digital landscape.
Exploring the Frontend
Once you’ve grasped the basics, it’s time to delve deeper into the frontend realm. From responsive design to user interface (UI) development, there’s no shortage of skills to master. CSS frameworks like Bootstrap and Tailwind CSS streamline the design process, allowing developers to create visually stunning layouts with ease. Meanwhile, JavaScript libraries such as React, Angular, and Vue.js empower developers to build dynamic and interactive frontend experiences.
Embracing Backend Technologies
While the frontend handles the visual aspect of a website, the backend powers its functionality behind the scenes. In this section of The Ultimate Guide to Web Development, we explore the world of server-side programming and database management. Popular backend languages like Python, Node.js, and Ruby on Rails enable developers to create robust server-side applications, while databases such as MySQL, MongoDB, and PostgreSQL store and retrieve data efficiently.
Mastering Full-Stack Development
With a solid understanding of both frontend and backend technologies, aspiring developers can embark on the journey of full-stack development as a Software Development company in USA. Combining the best of both worlds, full-stack developers possess the skills to build end-to-end web solutions from scratch. Whether it’s creating RESTful APIs, integrating third-party services, or optimizing performance, mastering full-stack development opens doors to endless possibilities in the digital landscape.
Optimizing for Performance and Accessibility
In today’s fast-paced world, users expect websites to load quickly and perform seamlessly across all devices. As such, optimizing performance and ensuring accessibility are paramount considerations for web developers. From minimizing file sizes and leveraging caching techniques to adhering to web accessibility standards such as WCAG (Web Content Accessibility Guidelines), every aspect of development plays a crucial role in delivering an exceptional user experience.
Staying Ahead with Emerging Technologies
The field of web development is constantly evolving, with new technologies and trends emerging at a rapid pace. In this ever-changing landscape, staying ahead of the curve is essential for success. Whether it’s adopting progressive web app (PWA) technologies, harnessing the power of machine learning and artificial intelligence, or embracing the latest frontend frameworks, keeping abreast of emerging technologies is key to maintaining a competitive edge.
Collaborating with a Software Development Company in USA
For businesses looking to elevate their online presence, partnering with a reputable software development company in USA can be a game-changer. With a wealth of experience and expertise, these companies offer tailored solutions to meet the unique needs of their clients. Whether it’s custom web development, e-commerce solutions, or enterprise-grade applications, collaborating with a trusted partner ensures seamless execution and unparalleled results.
Conclusion: Unlocking the Potential of Web Development
As we conclude our journey through The Ultimate Guide to Web Development, it’s clear that mastering the art of web development is more than just writing code — it’s about creating experiences that captivate and inspire. Whether you’re a novice coder or a seasoned veteran, the world of web development offers endless opportunities for growth and innovation. By understanding the fundamental principles, embracing emerging technologies, and collaborating with industry experts, you can unlock the full potential of web development and shape the digital landscape for years to come.
2 notes
·
View notes
Text
Getting Started with Full-Stack Web Development: Obstacles and Opportunities
Embarking on the journey to becoming a full-stack web developer offers a blend of exhilarating challenges and rewarding accomplishments. In this guide, we'll explore the intricacies of mastering full-stack development, delving into the obstacles you may face along the way and the triumphs that await those who persevere.

Introduction
Mastering full-stack web development is akin to embarking on a thrilling adventure—one that promises countless opportunities for growth, innovation, and professional fulfillment. However, the road to proficiency is not without its hurdles. In this blog, we'll navigate through the challenges aspiring full-stack developers may encounter, as well as the triumphs that come with overcoming them.
1. Diverse Skill Set
Full-stack web development demands proficiency in a diverse range of skills, spanning from frontend technologies like HTML, CSS, and JavaScript to backend languages such as Python, Ruby, or Node.js. Additionally, expertise in databases, server management, and deployment processes is crucial. Acquiring mastery in these areas requires dedication, time, and a continuous commitment to learning and adaptation.
2. Ever-Evolving Landscape
The realm of web development is in a perpetual state of evolution, with new frameworks, libraries, and tools emerging at a rapid pace. Keeping pace with these advancements and constantly updating your skill set is imperative to remain competitive in the industry. Allocate time to explore emerging technologies, enroll in online courses, and engage with the developer community to stay ahead of the curve.
3. Complexity of Projects
Full-stack developers often tackle intricate projects that necessitate the integration of various technologies and components. Managing the intricacies of these projects, troubleshooting issues, and ensuring seamless interaction between frontend and backend systems can be daunting. Nonetheless, overcoming these challenges cultivates invaluable problem-solving skills and deepens your comprehension of web development principles.
4. In-Depth Understanding
To excel as a full-stack developer, a profound understanding of programming concepts, algorithms, and data structures is indispensable. Mastery of these foundational principles empowers you to write concise, efficient code and tackle complex technical challenges with confidence. Dedicate time to delve into computer science fundamentals and engage in coding exercises to fortify your expertise.
5. Effective Problem Solving
Effective problem-solving is a hallmark of successful full-stack developers. Debugging code, identifying bottlenecks, and optimizing performance demand astute analytical skills and a systematic approach. Collaborating with peers, leveraging online resources, and seeking mentorship can facilitate the navigation of complex technical hurdles and yield effective solutions.
6. Strategic Time Management
Balancing multiple responsibilities, including frontend and backend development, database management, and project deployment, necessitates adept time management skills. Prioritize tasks, establish realistic timelines, and leverage productivity tools to streamline your workflow and maximize productivity. Reserve time for ongoing learning and professional development to continually enhance your skill set.
7. Cultivating Team Collaboration
Full-stack developers often collaborate with interdisciplinary teams, comprising designers, frontend developers, backend developers, and other stakeholders. Effective communication, teamwork, and collaboration are vital for project success. Foster strong interpersonal relationships, actively contribute in team settings, and cultivate a culture of open communication and collaboration within your team.
8. Prioritizing Security
Understanding security best practices and implementing robust security measures is paramount in web development. Full-stack developers must remain vigilant in identifying and mitigating security vulnerabilities to safeguard sensitive data and uphold the integrity of web applications. Stay informed about prevalent security threats, adhere to industry best practices, and consistently update your knowledge to proactively address emerging risks.
Conclusion
Embarking on the journey to becoming a full-stack web developer is a thrilling endeavor marked by challenges and triumphs. By embracing the obstacles, refining your skills, and maintaining a steadfast commitment to learning and growth, you can unlock a realm of opportunities and embark on a gratifying career in web development. Remember, each challenge surmounted brings you closer to mastery, and the journey itself is as enriching as the destination.
#full stack developer#education#information#full stack web development#web development#front end development#full stack developer course#technology#backend
2 notes
·
View notes